Intelligent User Manager (IUM) - SAML Support
Introduction
In most Data Center there is an SSO support required. Most common SSO is SAML.
We added SAML Support to our IUM Apps.
For Details see below.
Originally the user is in the disabled group, not beeing able to access Jira
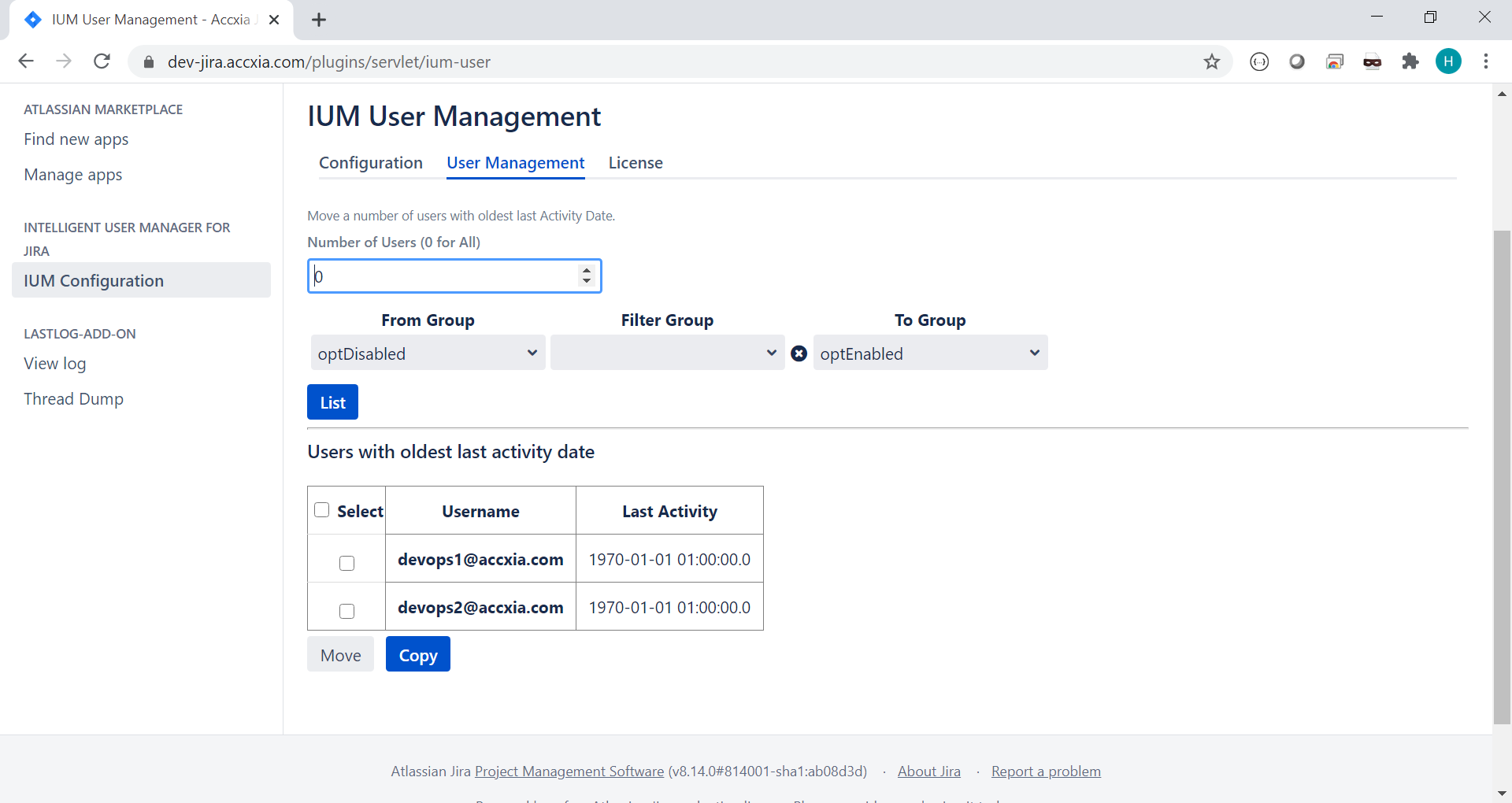
IUM cares about SAML.
So when a User logges in he is first enabled by IUM and later on authenticated via SSO.
Let's try to use this Url
https://dev-jira.accxia.com/secure/Dashboard.jspa
1st logIn at Google
Now see what happens
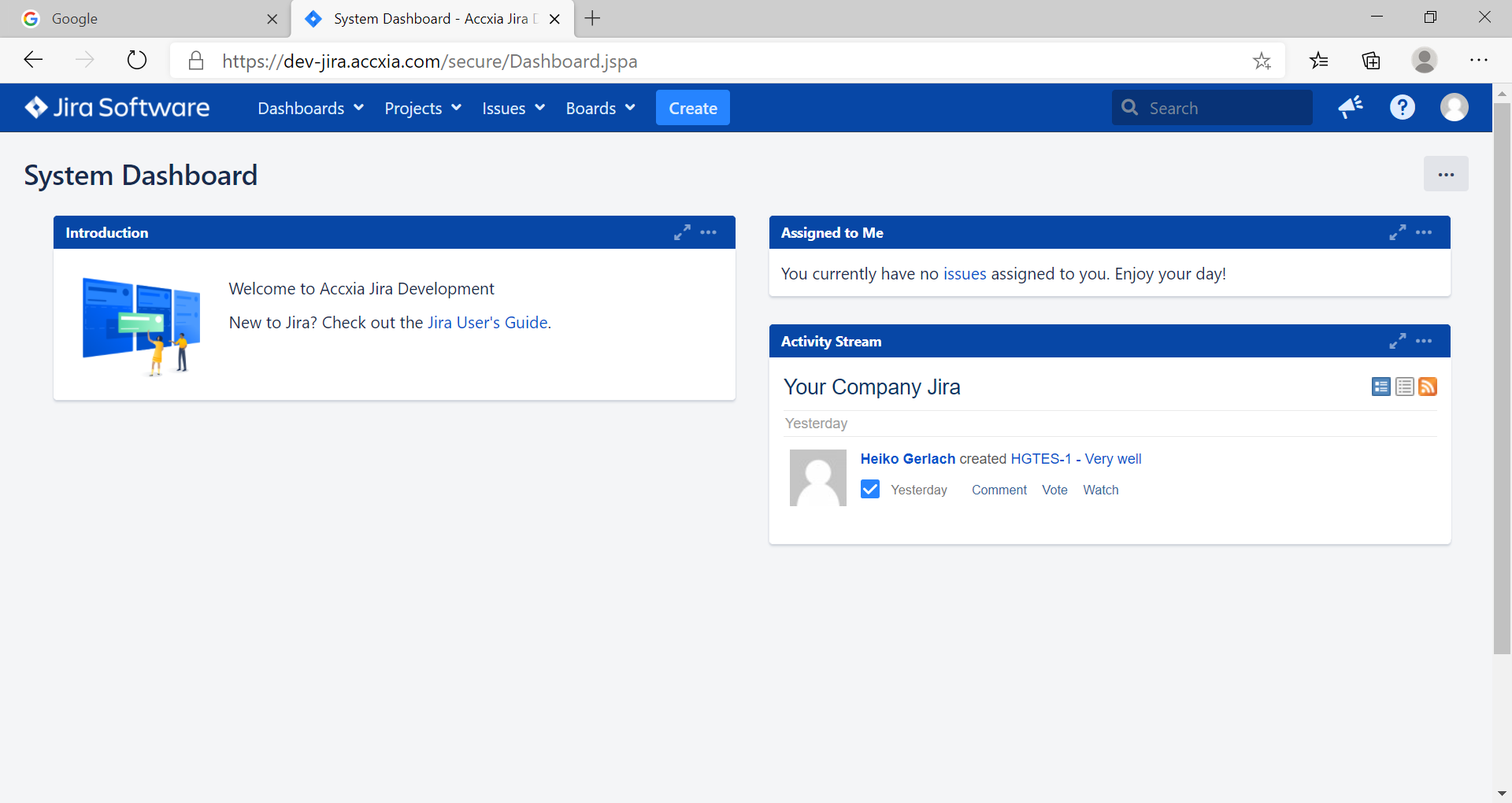
WE ARE IN
Let's verify the Enabled Group and see whe are in
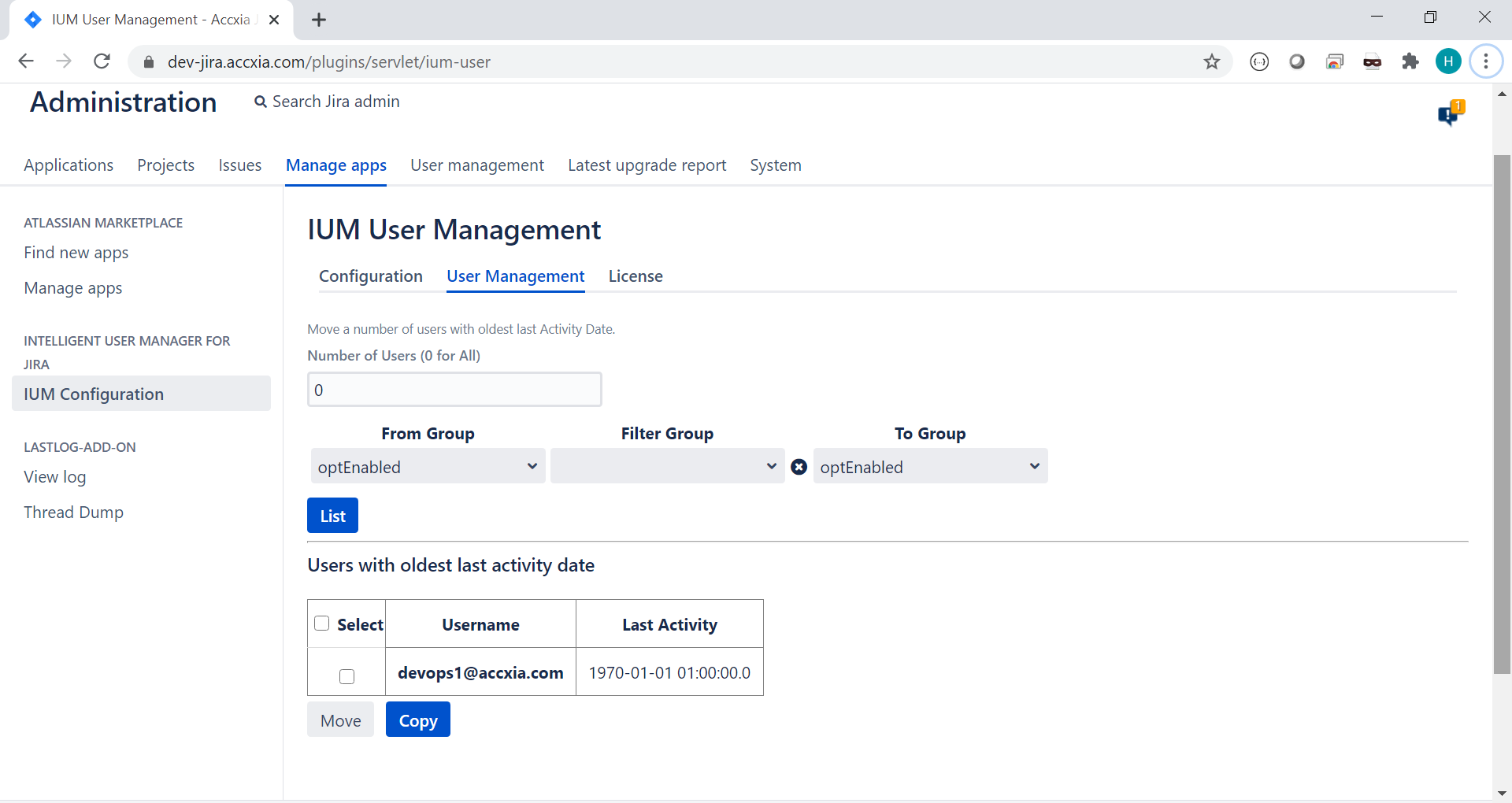
Background: Implementing with Google SAML as Identity Provider
Generic Solution using 2 IDPs
We have to create 2 IDP
- IDP Account 1 is responsible for IUM
- IDP Account 2 is responsible for SSO Authentication
IDP Account 1 must point to "https://dev-jira.accxia.com/plugins/servlet/samlium".
IDP Account 2 must point to "https://dev-jira.accxia.com/plugins/servlet/samlconsumer".
The Jira SSO.20 must be configured to the IUM Servlet via the IDP Account1. The Identity "provider single sign-on URL" must point to Account1
The IUM Servlet redirects to Account 2 (SSO) (can be configured in future)
Using it this way, we have created a full generic Solution
Solution with just 1 IDP (prefered Option)
Ideally there is just one IDP required.
We have created a second solution. This solution uses a Servletfilter instead of a Servlet. The servlet filter intercepts the url "/plugins/servlet/samlconsumer" and enables the IUM User.
The IDP must be configured with https://dev-jira.accxia.com/plugins/servlet/samlconsumer.
After enabling the user successfully a redirect is sent to "/plugins/servlet/external-login".
As a result the User is logged in.
Note:
- Currently SAML is only supported for uncrypted SAML Messages. This can be developed later on to support crypted Messages as well.
- Atlassian SSO2.0 supports primary and first Authentication, OUR IUM App supports both options
Jira 10.3.x
From Jira 10.3.x onwards, either Service Management logins must be selected for the respective authentication method or the corresponding entries must be made under SAML 2.0 SSO in the IUM settings.
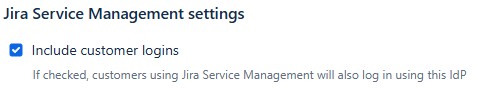
Service Management logins
- Authenication methods
- select the appropriate login option
- edit
- Select include customer logins
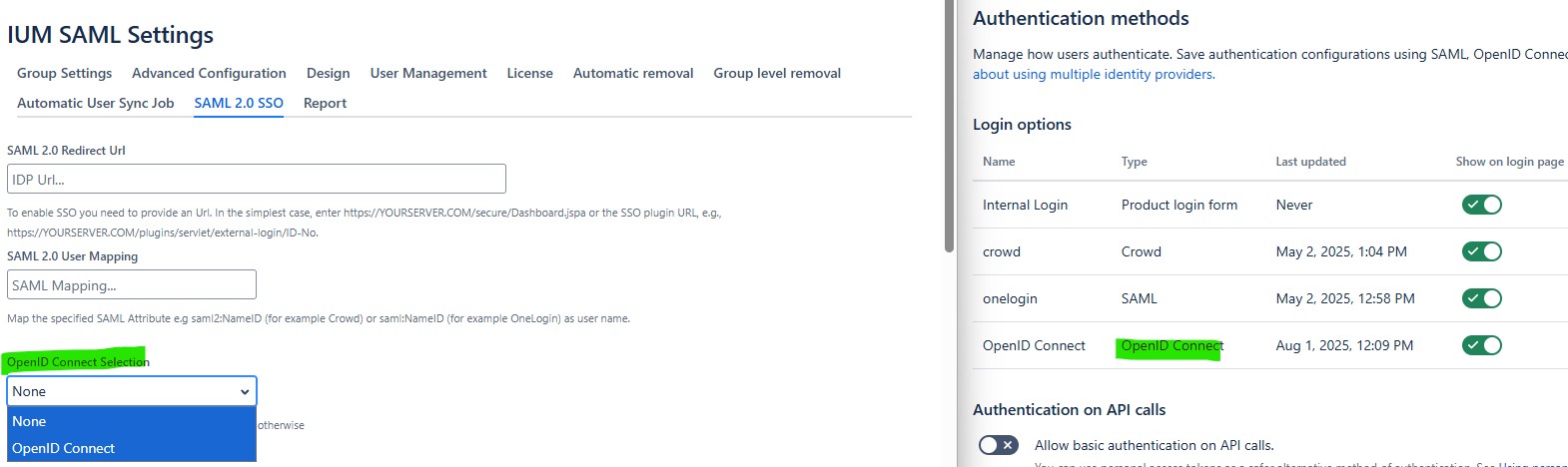
IUM settings SAML 2.0 SSO
- go to ium SAML settings
- SAML 2.0 Redirect Url
enter https://YOURSERVER.COM/secure/Dashboard.jspa or https://YOURSERVER.COM/plugins/servlet/external-login/ID-No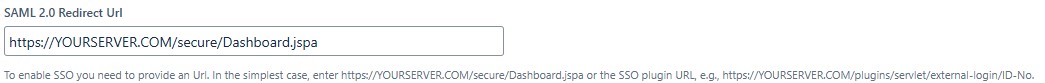
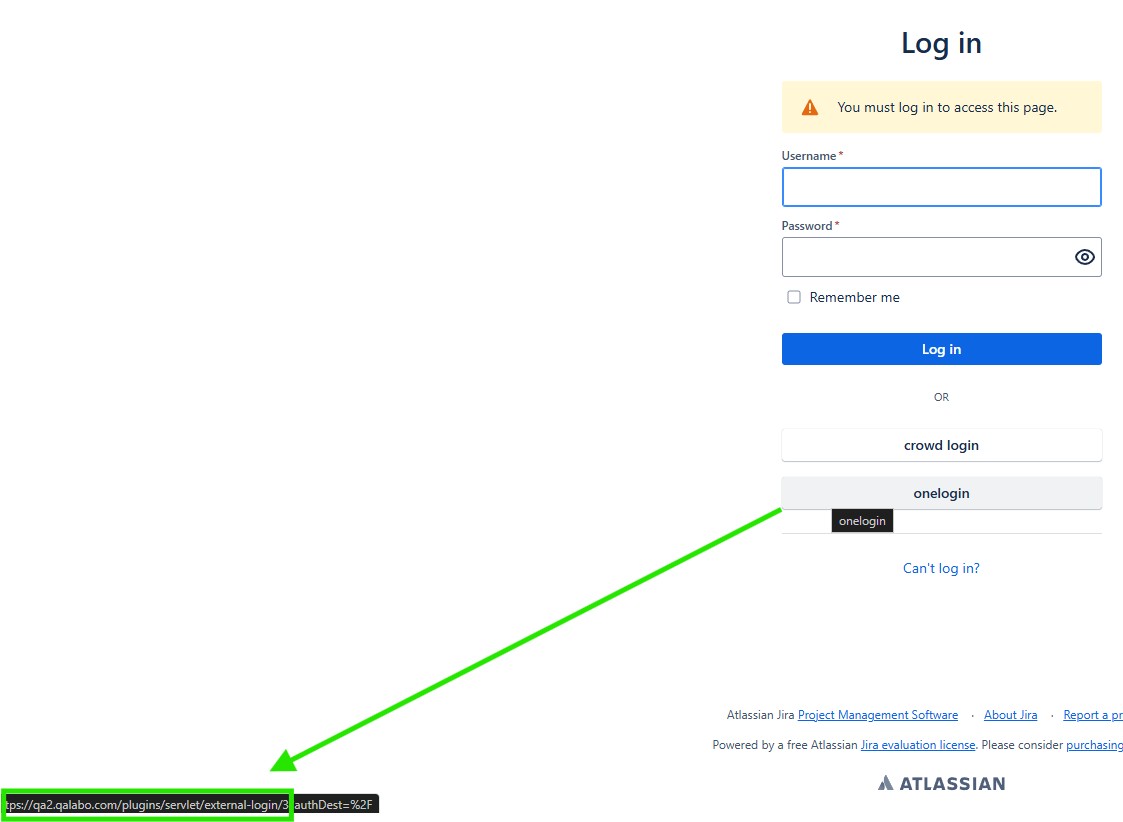
- SAML 2.0 User Mapping
enter saml2:NameID (for example Crowd) or saml:NameID (for example OneLogin)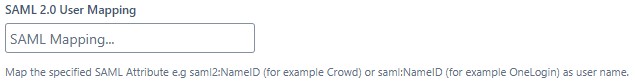
Authentication methods with OpenID Connect (from IUM4Jira 5.3.2)
- go to ium SAML settings
- The corresponding entry must be selected under OpenID Connect Selection.